

Who are you? What system capabilities are you permitted? If you leave the company, what accesses need to be removed?.
Ver Fuente Visitas: 224.721
Cybersecurity Architecture Cybersecurity Architecture Who Are

Exploring the realms of .
Ver Fuente Visitas: 52.725

Identity is everything. So, you need to treat every .
Ver Fuente Visitas: 192.233

You can lock down MS Team files more than just the standard read-write .
Ver Fuente Visitas: 17.782

Do you really know what is identity and .
Ver Fuente Visitas: 23.452

- - - - - An important aspect of security is to match the right permissions to the right people at the right time. In this video, you'll learn ....
Ver Fuente Visitas: 60.072

- - - - - There are many different ways to provide authorization, rights, and permissions. In this video, you'll learn about least ....
Ver Fuente Visitas: 49.172

Identity and .
Ver Fuente Visitas: 114.619

🎉 🔥 Oferta especial: ¡Consigue mi curso de Udemy con descuento! 🔥 🎉 🚀 ¡Domina Azure como un profesional! - https://www.udemy ....
Ver Fuente Visitas: 482

Contact Us: Portland Metro 503-468- 5824 5862 Lakeview Boulevard Lake Oswego, OR 97035 SW Washington 971-314-6571 ....
Ver Fuente Visitas: 44.762


Looking to allow other users to query your datasets in BigQuery? In this episode of BigQuery Spotlight, we show you how you can ....
Ver Fuente Visitas: 40.071

Role-Based .
Ver Fuente Visitas: 65.306

In this video on what is IAM, we will look into Identity and .
Ver Fuente Visitas: 109.236

What is Privileged .
Ver Fuente Visitas: 19.307

Security+ Training Course Index: https://professormesser.link/sy0601 Professor Messer's Course Notes: ....
Ver Fuente Visitas: 90.513

Learn how to .
Ver Fuente Visitas: 7105
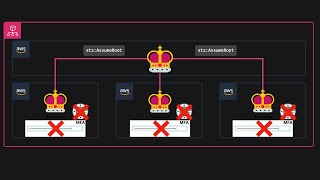
This is how you should centrally .
Ver Fuente Visitas: 1379

In this AWS video tutorial, you'll learn about the different methods of implementing .
Ver Fuente Visitas: 88.615
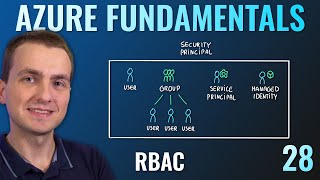
Azure Role-based .
Ver Fuente Visitas: 236.675